The loss of data can bring an enterprise down – be it for a few hours, days, or even weeks. For smaller businesses, data loss can be devastating. For home users, it can be heart-breaking and utterly annoying. Whatever brings about data loss is bound to cause an organization to suffer – not only from the loss of the data itself but from loss in employee productivity during the time it takes to restore information from a backup set. Having said this, it becomes clear that backup is, without a doubt, one of the most significant aspects of a business continuity plan.
Essentially the term “backup” means a duplicate copy of key information, both physical (paper) and computer records. An organization must create a decent set of backup procedures to ensure that data is protected, and then follow them to a Tee.
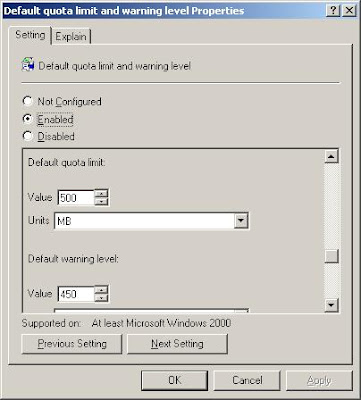
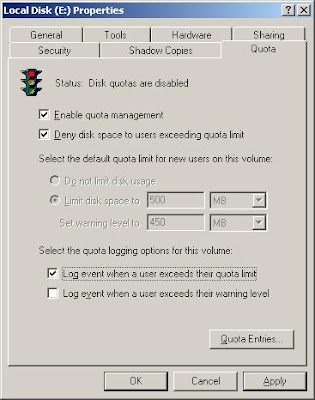
Vital paper records that should be stored safely include tax records, financial statements, contracts, personnel information, and corporate documents. Data that should be backed up regularly includes, but is not limited to, e-mail correspondence, audit files, user information, utilities and applications, operating systems, financial data and databases, as well as customer lists. Ideally every byte of data on every system in an organization would be backed up every night. In today’s world this is not a realistic possibility – due to a lack of time and resources. These days, you are obliged to choose what will or won’t be backed up, based on the importance of the data.
Planning for Backup and Recovery
When planning for backup and recovery, you must ask yourself a number of questions to help you make a decision on how, when and what data will be backed up. These include the following:
When is the most convenient time to schedule backups?
Backing up data should ideally be done at off-peak hours when system usage is low. However, due to the type of data being backed up this is not always possible. Considerations must be made as to when key system data is to be backed up.
Will you store backups off-site?
It is highly recommended that backup media (containing data) is stored off-site in case of a natural disaster, fire, leak, etc. It would also be wise to keep a copy of the software required to install and restore operating systems, database servers, backup recovery, and so on.
How important is the data your systems contain?
Classifying the importance of your data will help you decide if the data needs to be backed up, how it should be backed up and when it should be backed up. Critical data (such as financial data, databases, etc) will take priority and should have a long-term redundant backup set, whereas data of less importance should be backed up daily and easily be recoverable.
How fast will restoring data from backup need to be?
Bringing a critical system back online would normally be done as soon as possible. Your backup plan depends a lot on the time it takes to recover a system. Data should be classified by priority and restored in sequence.
How regularly does data change?
Data that changes daily should be backed up daily. The rate at which your data changes will reflect your decision on how often the data should be backed up.
What type of information does the data residing on the systems contain?
As well as knowing what information the data contains so that you can identify it as critical, confidential, etc, it’s important to note that although data may not seem important to you, it might be to someone else. This will help you determine when and how certain data should be backed up.
Do you have what’s necessary to perform backups?
Make sure that you have the right hardware and enough media needed to perform a backup. Choosing backup media is an important factor in the backup and recovery process. Backup tapes are a common form of media since they can store large amounts of data and are cheap. They are however much slower than alternative options.
Types of Backup
Each file or folder on your system consists of what is called an Archive attribute. If this attribute is enabled then the file or folder may require backing up at the next backup time.
To view the archive attribute in Windows 2003, right click a file or folder and select properties. Press the Advanced button to bring up the Advanced Attributes dialog box. This will allow you to select whether you want the object to be ready for archiving.
There are five backup types which you can use depending on the importance of the data you are backing up and how convenient you want the restoration process to be.
Daily
Backs up files that have changed since the last daily backup. If a file is modified on the same day as the backup, it will be backed up. The archive attribute of the files is not changed.
Incremental
Backs up files that have changed since the most recent full (normal) or incremental backup. If the archive attribute is present then it means the file has been modified – only files with this attribute are backed up. Once the file has been backed up, the archive attribute is cleared and only set once the data has been modified again.
Full (Normal)
Backs up all files that have been selected, despite the archive attribute setting. Once the file has been backed up, the archive attribute is cleared until the file is modified. When the archive attribute is set again, it indicates that the file needs to be backed up.
Differential
Backs up files that have changed since the last Full backup. If the archive attribute is present, it means that the data has been modified and files having this attribute set will be backed up. However, in this case the attribute is not cleared so as to allow other types of backups to take place on this data at a later stage.
Copy
Backs up all files that have been selected, despite the archive attribute setting. The archive attribute is not changed, so that other types of backup can be performed on the same data.
Keep in mind:
A backup procedure is never considered complete until it has been fully tested. What good is it if you backup data but can’t restore it?
Types of Backup Media
The most common types of backup media available on the market today include:
Tape drives
Tape drives are the most common backup media around due to their low cost. The average capacity of a tape drive is 4 to 10 GB. The drawbacks are that they are relatively slow when compared with other media, and can tend to be unreliable. Magnetic tape cartridges are used to store the data, which leaves it susceptible to loss of information over time or through breaking/stretching the tape.
Disk drives
Disk drives are expensive but very fast compare to tape drives. The disk drive rotates at a very fast pace and has one or more heads that read and write data. If an organization is looking for a fast method of backup and recovery then disk drives are the way to go – the difference in speed between a tape drive and a disk drive is hours compared to minutes, respectively.
Removable Disks
Using a removable disk such as a ZIP/JAZ drive is becoming increasingly popular for the backup of single systems. They are quite fast, not that expensive and easy to install and carry around. The downside is that the capacity is usually (at the time of writing this article) not more than 2GB in size.